Custom VPCAmazon Virtual Private Cloud |
Summary
Creation of the VPCAmazon service that allows you to control the virtual networking environment. into which the resources to support the website and related data analysis will be launched.
Disclaimer
I am very much a newbie when it comes to networking so what is described below is what I did and not to be confused with what one should do. However even without being a security expert I'm pretty sure publishing the details of your implementation is frowned upon but I am willing to do this for two reasons (maybe three). First, none of the code or data stored in this VPCAmazon service that allows you to control the virtual networking environment. is in anyway sensitive. The code can be downloaded from BitBucketWeb-based service for hosting and sharing Git repositories. and the data is publicly available. Second, I struggled with a connectivity issue between EC2Amazon service that allows you to provision and configure your own servers. and RDSAmazon service for launching and managing relational databases. and it was difficult to find a comprehensive working example of how to set up the Route Tables, NACLs and Security Groups. So I've included what worked for me in case it is of use to others. (Third, I have a small hope that if I've done something horribly wrong some kind and knowledgeable person will drop me a line to let me know.)
Description
-
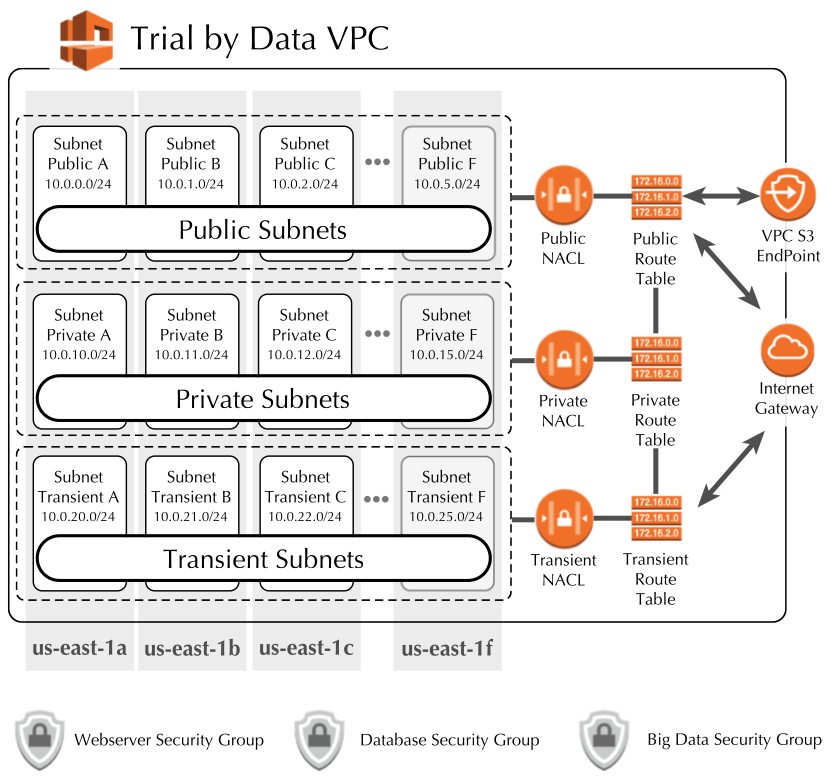
VPCAmazon service that allows you to control the virtual networking environment.
The VPCAmazon service that allows you to control the virtual networking environment. was created with the Name Tag of 'tbdVPCAmazon service that allows you to control the virtual networking environment.' and the CIDR Block to 10.0.0.0/16. This gives a range of addresses from 10.0.0.0 to 10.0.255.255, about 65,536 address minus the AWS reserved IPs. This is far more than enough for the purpose of this website and related tests and analysis.
-
Subnets
Three types of subnets were defined - Public, Private and Transient. The public subnets are intended for the EC2Amazon service that allows you to provision and configure your own servers. web server. The private subnets for the database. The transient subnets are for experimenting with services and resources short term, for example, launching an EMR cluster for data analysis or machine learning.
us-east-1a us-east-1b us-east-1c Public tbdSubnet_Public_A
10.0.0.0/24tbdSubnet_Public_B
10.0.1.0/24tbdSubnet_Public_C
10.0.2.0/24Private tbdSubnet_Private_A
10.0.10.0/24tbdSubnet_Private_B
10.0.11.0/24tbdSubnet_Private_C
10.0.12.0/24Transient tbdSubnet_Transient_A
10.0.20.0/24tbdSubnet_Transient_B
10.0.21.0/24tbdSubnet_Transient_C
10.0.22.0/24
There are currently 6 Availability Zones in my region - us-east-1a through us-east-1f. So far subnets have only been built out for the first three. Additional subnets will be added as needed following the same naming and CIDR block assignment conventions. The CIDR blocks are assigned so that the all public blocks have a single digit in the third position to make identification of public IPs easier.
-
Internet Gateway
Since the main goal is to create the website and make it available, an internet gateway with the name tag "tbdIGW" was created and attached to the tbdVPCAmazon service that allows you to control the virtual networking environment..
-
Routing Tables
AWS automatically creates a default routing table when the VPCAmazon service that allows you to control the virtual networking environment. is created. This routing table allows all local traffic (i.e. communications between subnets). This routing table was renamed to "tbdRoute_Private" and associated with all of the private subnets.
Another routing table with the name tag "tbdRoute_Public" was also created which allowed local traffic and traffic from the internet gateway. This routing table was associated with the public subnets.
The "tbdRoute_Transient" routing table has the same rules as the public routing table and was associated with the transient subnets.
Destination Target Public 10.0.0.0/16 local 0.0.0.0/0 Internet Gateway Private 10.0.0.0/16 local Transient 10.0.0.0/16 local 0.0.0.0/0 Internet Gateway -
S3Amazon's highly durable, highly available object storage. End Point
An S3Amazon's highly durable, highly available object storage. endpoint was added to the tbdVPCAmazon service that allows you to control the virtual networking environment. with full access rights. It was associated with the public subnets which automatically configured the public routing tables to add an entry to allow traffic via S3Amazon's highly durable, highly available object storage..
-
NACLs - Network Access Control Lists
AWS also automatically creates a default NACL which allows all traffic. This was modified to deny all traffic by deleting the existing inbound and outbound rules that allowed all traffic through and the NACL was renamed tbdNACL_None. This was done to avoid accidentally exposing a newly created subnet to unintended traffic as any new subnet will be assigned to this NACL.
A public NACL was created which allowed inbound traffic from HTTP, HTTPS from anywhere, SSH and RDP from my IP and a custom TCP from inside the VPCAmazon service that allows you to control the virtual networking environment.. Allowed outbound traffic includes HTTP, HTTPS and custom TCP. All public subnets were reassigned to this NACL.
The private NACL allows all traffic and was assigned to all the private subnets. (Since the private subnets only allow local traffic via the private routing table should be safe.) The transient NACL at this time only allows traffic from my IP.
NACL Direction Rule # Type Source Action Public Inbound 100 HTTP (80) 0.0.0.0/0 ALLOW 200 HTTPS (443) 0.0.0.0/0 ALLOW 300 SSH (22) my-ip ALLOW 400 RDP (3389) my-ip ALLOW 500 Custom TCP Rule
(1024-65535)10.0.0.0/16 ALLOW * ALL Traffic 0.0.0.0/0 DENY Outbound 100 HTTP (80) 0.0.0.0/0 ALLOW 200 HTTPS (443) 0.0.0.0/0 ALLOW 300 Custom TCP Rule
(1024-65535)0.0.0.0/0 ALLOW * ALL Traffic 0.0.0.0/0 DENY Private Inbound 100 ALL Traffic 0.0.0.0/0 ALLOW * ALL Traffic 0.0.0.0/0 DENY Outbound 100 ALL Traffic 0.0.0.0/0 ALLOW * ALL Traffic 0.0.0.0/0 DENY Transient Inbound 100 ALL Traffic my-ip ALLOW * ALL Traffic 0.0.0.0/0 DENY Outbound 100 ALL Traffic 0.0.0.0/0 ALLOW * ALL Traffic 0.0.0.0/0 DENY -
Security Groups
A default security group that allows all traffic from itself is created automatically when a VPCAmazon service that allows you to control the virtual networking environment. is created. In addtion two other security groups were created - tbdSecurity_Webserver and tbdSecurity_Database.
Security Group Direction Type Source Description tbdSecurity_Default Inbound ALL Traffic group-id of
tbdSecurity_DefaultAll Traffic from itself Outbound ALL Traffic 0.0.0.0/0 tbdSecurity_Webserver Inbound HTTP (80) 0.0.0.0/0 HTTP from Anywhere HTTPS (443) 0.0.0.0/0 HTTPS from Anywhere SSH (22) my-ip SSH from me Outbound ALL Traffic 0.0.0.0/0 tbdSecurity_Database Inbound MySQLRelational database used to hold website content and search data./Aurora (3306) group-id of
tbdSecurity_WebserverAll Traffic from Webserver Security Group Outbound ALL Traffic 0.0.0.0/0